Scalable Validation of System-on-Chip Vulnerabilities using Security Assertions |
Overview
System-on-Chip (SoC) is the brain behind the
computing devices today. Unlike microcontroller
based designs in the past, even resource constrained
Internet-of-Things (IoT) devices nowadays
incorporate one or more complex SoCs. As
shown in the following figure, a typical SoC consists of
multiple Intellectual Property (IP cores) including
processor, memory, network-on-chip, controllers,
converters, input/output devices, etc. Drastic increase
in SoC complexity has led to significant increase in SoC design and validation complexity. Reusable hardware IP based
SoC design has emerged as a pervasive design practice in the industry to dramatically reduce design and verification cost
while meeting aggressive time-to-market constraints. Growing reliance on these pre-verified hardware IPs, often gathered
from untrusted third-party vendors, severely affects the security and trustworthiness of SoC computing platforms. Hardwarelevel
vulnerabilities should be fixed before deployment since it affects the overall system security. Based on CVE-MITRE
estimates, if hardware-level vulnerabilities are removed, the overall system vulnerability will reduce by 43%.
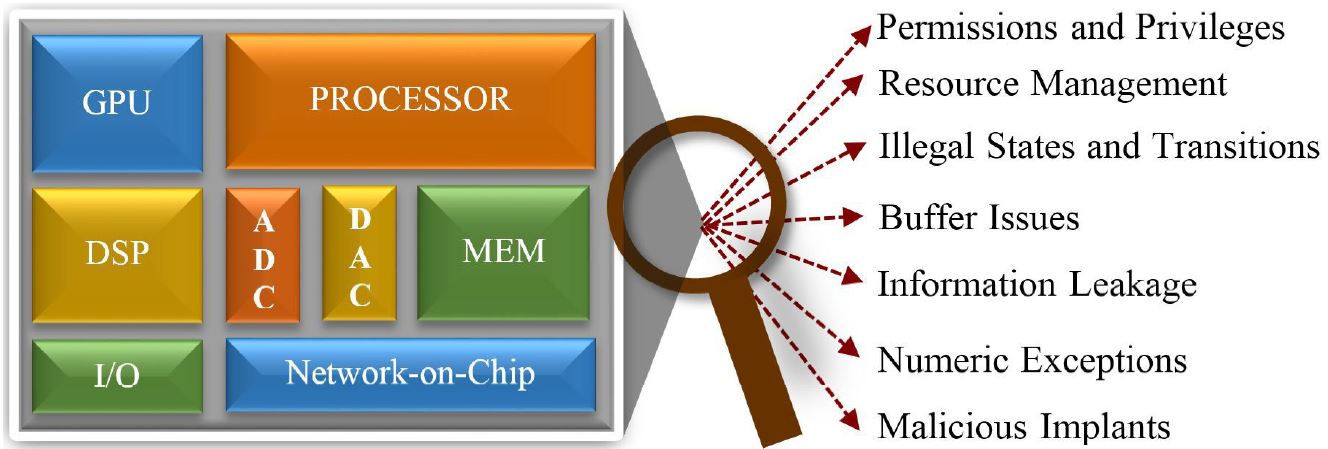
While the existing efforts on SoC security validation have shown promising results, they have
three major drawbacks. (1) The existing trust validation approaches primarily target malicious modifications (e.g., hardware
Trojans), which represent only one out of many classes of vulnerabilities outlined in the US National Vulnerability Database. (2) While there is a vast literature on both software and hardware assertions for monitoring functional scenarios,
there is limited effort in utilizing assertions to monitor SoC security vulnerabilities. (3) Even millions of random or
constrained-random tests may not be able to activate security assertions that are based on complex and rare scenarios.
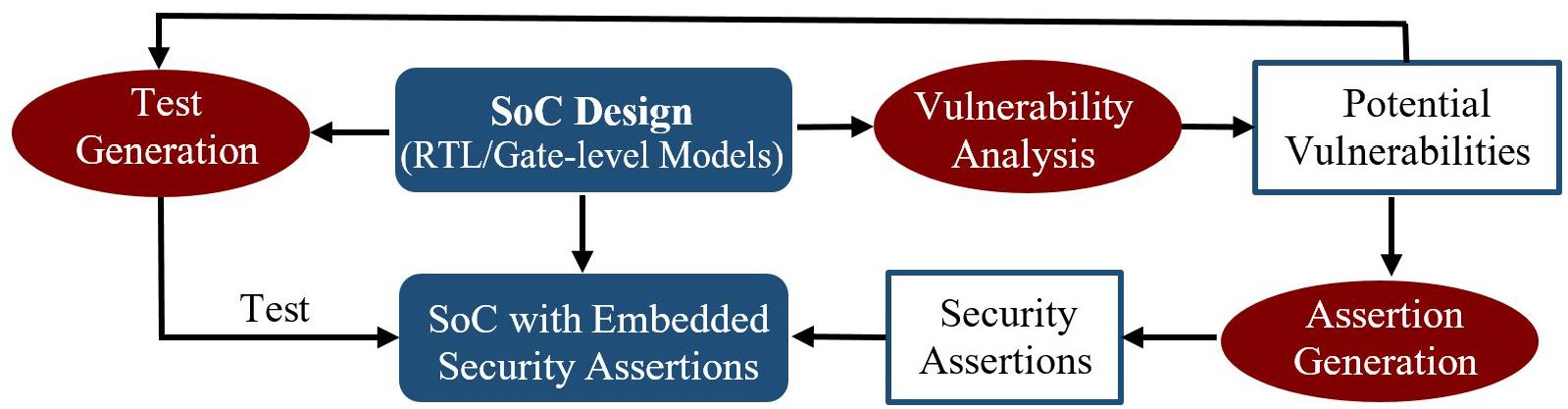
Project Vision: The goal of this proposal to develop a comprehensive and scalable framework for verifying SoC vulnerabilities
using security assertions. The following figure shows three major steps in our proposed SoC security validation framework. The
outcome is a comprehensive and automated methodology for SoC security validation that (1) can be employed early in
the SoC design life-cycle, (2) enables automated validation of security vulnerabilities utilizing security assertions, and
(3) allows seamless integration in the existing industrial flows with assertion-based validation. A successful implementation
of this research will have a significant impact in industry as well as in academic research to explore innovative ways of
utilizing assertions for both functional and security validation in designing secure and trustworthy SoCs.
Members
Downloads
The software with documentation can be downloaded from
GitHub.
Publications
Journal Articles:
| J2 |
Hasini Witharana, Yangdi Lyu, Subodha Charles and Prabhat Mishra, A Survey on Assertion-based Hardware Verification, ACM Computing Surveys (CSUR), 2022. |
| J1 |
Hasini Witharana, Yangdi Lyu and Prabhat Mishra, Directed Test Generation for Activation of Security Assertions in RTL Models, ACM Transactions on Design Automation of Electronic Systems (TODAES),a26(4), article 26, pages 1-28, 2021. |
Referred Conference Papers:
| C4 |
Hasini Witharana and Prabhat Mishra, Speculative Load Forwarding Attack on Modern Processors, SRC TECHCON, 2022. |
| C3 |
Aruna Jayasena and Prabhat Mishra, Network-on-Chip Trust Validation using Security Assertions, SRC TECHCON, 2022. |
| C2 |
Hasini Witharana and Prabhat Mishra, Automated Generation of Security Assertions for RTL Models, SRC TECHCON, 2021. |
| C1 |
Hasini Witharana and Prabhat Mishra, Test Generation for Activation of Assertions in RTL Models, SRC TECHCON, 2020. |
Research Sponsors
 |
This project is funded by the Semiconductor Research Corporation (SRC). The views expressed on the site are those of the members of
this project and do not necessarily represent those of the Semiconductor Research Corporation. |


