SoC Trust Verification using Security Assertions and Checkers |
Overview
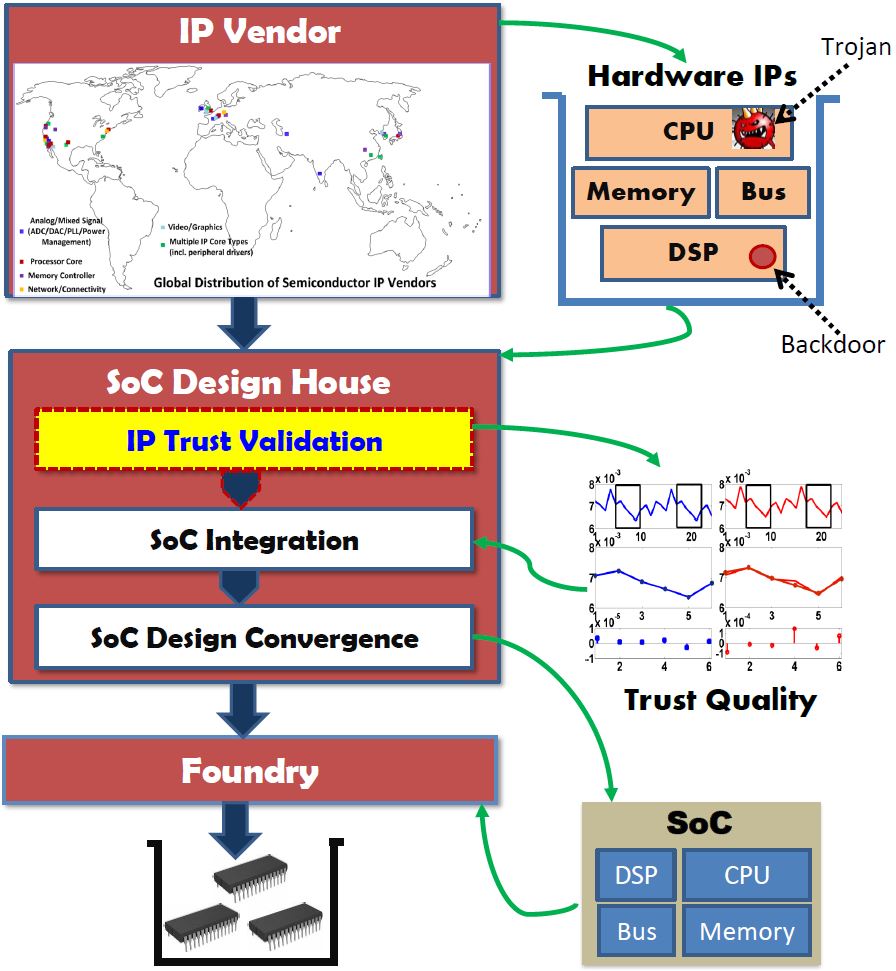
Reusable hardware Intellectual Property (IP) based System-on-Chip (SoC) design has emerged
as a pervasive design practice in the industry to dramatically reduce design/verification
cost while meeting aggressive time-to-market constraints. However, growing reliance on these
pre-verified hardware IPs, often gathered from untrusted third-party vendors, severely affects
the security and trustworthiness of SoC computing platforms. An important emerging concern
with the hardware IPs acquired from external sources is that they may come with deliberate
malicious implants to incorporate undesired functionality (e.g. hardware Trojan), undocumented
test/debug interface working as hidden backdoor, or other integrity issues (e.g. rare input
conditions that violate peak power or temperature constraints). SoC designers typically tend
to treat these IPs as black box and rely on the IP vendors on their structural/functional
integrity. However, recent investigations by researchers including the PIs as well as reported
incidences show that such practices make SoCs increasingly vulnerable to trust issues and
highlight the impending threat. It is extremely difficult to verify integrity and trust for
hardware IPs of different types and complexity, due to (a) incomplete functional specifications,
and (b) lack of a golden reference model. Even if such a model is available from an IP vendor,
its integrity remains questionable. To address this critical need, in this project, we investigate
a comprehensive scalable framework for IP trust verification through integration of trust
analysis with a unified functional-structural-parametric trust validation scheme, and effective
IP trust metrics.
Members
Research Sponsors
 |
This project is funded by (Cisco). The views expressed on the site are those of the members of
this project and do not necessarily represent those of Cisco. |


